5 Safe VPN Alternatives for Enhanced Online Privacy
In today’s digital landscape, safeguarding your online privacy is crucial. A significant number of users turn to Virtual Private Networks (VPNs) for secure browsing and to bypass geographical content restrictions. However, it’s important to acknowledge that VPNs come with their own set of challenges. They can sometimes hinder your internet speed, carry hefty price tags, and might not always meet expectations. If you’re tired of the common VPN inconveniences, exploring alternatives that align better with your preferences could be beneficial. Here are five alternatives to VPNs that you might find more suitable.
Understanding VPNs and the Reason to Explore Other Options

Image Credit: Pixabay.com
A VPN, or Virtual Private Network, serves to encrypt your internet traffic and conceal your IP address by routing it through a server located elsewhere. While this provides an added layer of privacy, it may not be the best solution for every user.
VPN Drawbacks
- Possible slowdown in internet speed due to encryption.
- Premium VPN services can be quite costly.
- Certain sites may block VPN connections.
- Setting up VPNs can be complex for those less tech-savvy.
Advantages of Considering Other Options
By looking beyond traditional VPN options, you might uncover alternative solutions offering enhanced speed, lower costs, and greater flexibility, all while ensuring your online privacy remains intact.
Five Secure VPN Alternatives Worth Considering
1. Explore Smart DNS
Smart DNS is a straightforward solution for accessing geo-restricted content while maintaining fast performance. Unlike VPNs, Smart DNS does not provide encryption; it simply redirects your DNS requests through its servers.
How Smart DNS Functions
This technology modifies your device’s DNS settings to use its own, enabling you to visit blocked websites as if you were connecting from a different location. It’s particularly effective for streaming and accessing restricted websites.
Pros of Using Smart DNS
- Enhanced speeds since encryption is not utilized.
- Perfect for gaming and streaming activities.
- Ease of setup across various devices.
Cons of Smart DNS
- No IP address concealment, making your real IP identifiable.
- Lacks encryption, which can limit security.
Steps to Implement Smart DNS
- Select a Smart DNS provider, such as Unlocator or Smart DNS Proxy.
- Register and obtain DNS addresses from your chosen provider.
- Navigate to your device’s DNS settings (generally found in network settings).
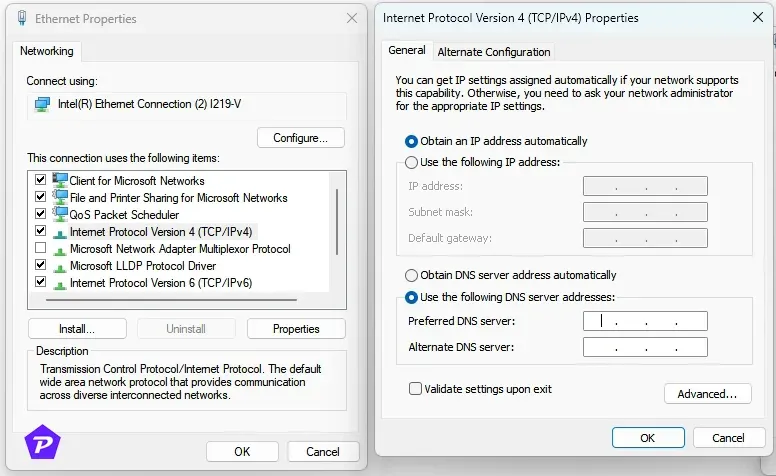
- Input the provided DNS addresses.
- Restart your device to implement the changes.
2. Utilize a Proxy Server
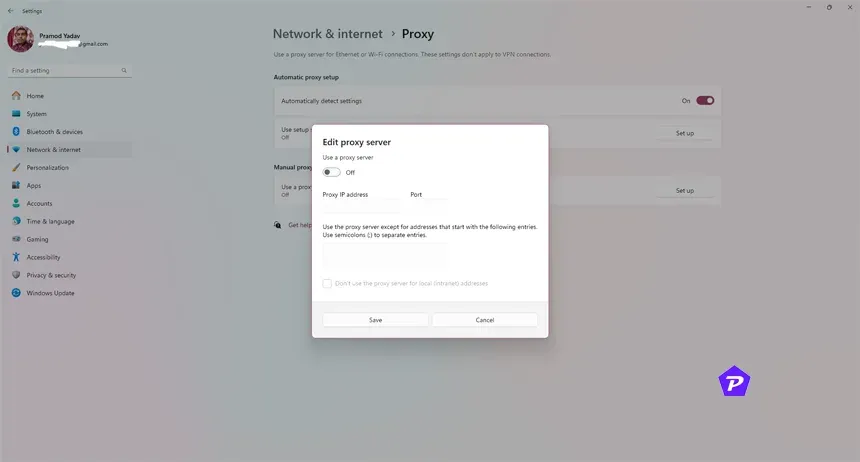
A proxy server acts as an intermediary between your device and the internet, obscuring your IP address by forwarding your traffic through its own address, which makes your online presence less traceable.
Different Types of Proxy Servers
- HTTP Proxy: Well-suited for web browsing.
- HTTPS Proxy: Offers encryption for safe browsing.
- SOCKS Proxy: More versatile, though potentially slower.
Benefits of Proxy Servers
- Generally budget-friendly, with numerous free options available.
- Aids in evading geo-restrictions.
- Enables anonymous browsing.
Drawbacks of Proxy Servers
- Free versions often come with slow and inconsistent performance.
- Lack of encryption reduces overall security.
Configuring a Proxy Server
- Select a Proxy service like Tuxler Proxy or KProxy.
- Adjust your device or browser settings to integrate the proxy.
- Input the proxy’s IP address along with the port number.
- Save your changes and begin browsing using the proxy.
- Unlocking ExtraTorrents: Proxy Sites List
- What Are the Differences Between Tor, VPN, and Proxy?
3. Accessing Websites with Tor
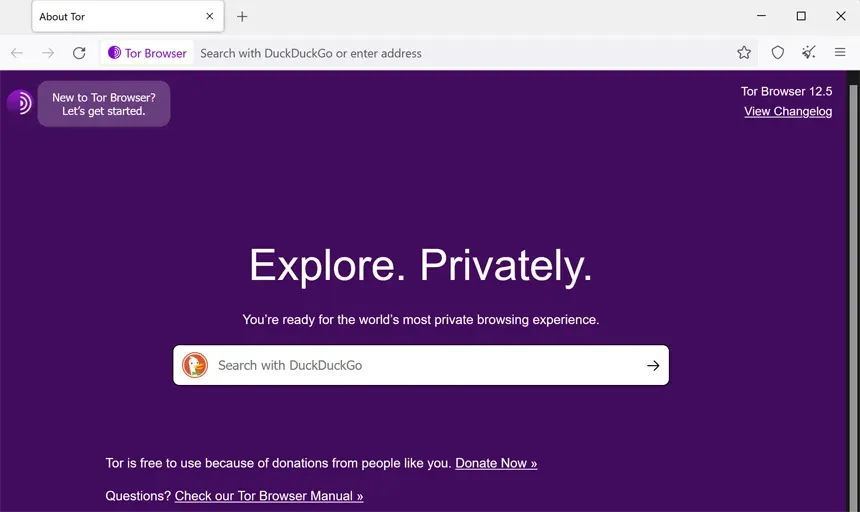
Tor, short for “The Onion Router,” is focused on ensuring user anonymity. It anonymizes your internet traffic by routing data through multiple volunteer-run servers, encrypting the data at each layer, which makes it exceptionally difficult to track.
Understanding Tor for Anonymity
Advantages of Tor
- Provides a high degree of anonymity.
- Free to utilize.
- Great for accessing sensitive information.
Disadvantages of Tor
- Browsing speeds can be reduced.
- Not recommended for streaming or gaming.
- Some websites actively block Tor users.
Guidelines for Safe Tor Usage
- Download the Tor Browser from the official website.
- Refrain from installing additional plugins that might jeopardize your anonymity.
- Keep default settings unless you have advanced knowledge.
- Consider using Tor bridges if your Internet Service Provider (ISP) blocks access to Tor.
4. Using Remote Desktop
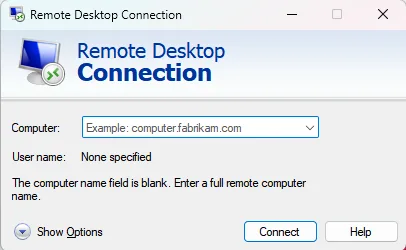
Remote desktop applications let you control a computer located elsewhere, facilitating access to region-specific content through a virtual machine (VM) based in that area.
Mechanism of Remote Desktops
By obtaining a VM from providers like AWS or Google Cloud, users can browse as if they are physically located in the VM’s area—allowing for an experience akin to using a computer situated in another country.
Benefits of Remote Desktop Solutions
- Effortlessly access geo-restricted content.
- Ensures a high level of privacy.
- Offers flexibility to meet varying needs.
Drawbacks of Remote Desktop Solutions
- Complex setup may be required.
- Maintenance can be time-intensive.
- Costs can rise when utilizing cloud services.
Getting Started with Remote Desktop Connection
- Select a cloud service provider (e.g., AWS, Google Cloud).
- Create a VM in your desired geographical region.
- Install remote desktop software (e.g., Microsoft Remote Desktop, TeamViewer).
- Connect to the VM using your remote desktop application of choice.
- Secure the VM with strong passwords and enable multi-factor authentication.
5. Implementing SSH Tunneling
SSH (Secure Shell) tunneling enables you to establish a secure and encrypted connection between your device and a remote server, catering especially to tech-savvy individuals looking for robust security.
Secure Browsing with SSH
SSH tunneling encrypts all traffic via a secure channel, providing an additional privacy layer similar to that of VPNs.
Advantages of SSH Tunnels
- Offers strong encryption.
- Can mask your IP address.
- Ideal for securely accessing remote services.
SSH Challenges and Limitations
- Setup may be complex for novices.
- Requires access to a remote server.
- Potentially slower than browsing without encryption.
Establishing an SSH Tunnel
- Select an SSH client (like PuTTY for Windows or Terminal for macOS/Linux).
- Connect to a remote server (login credentials will be necessary).
- Input the relevant command to start the SSH tunnel.
- Adjust your browser settings to funnel traffic through the tunnel.
- Conduct tests to confirm that the connection is secure.
Evaluating VPN Alternatives: Which is the Best Choice for You?
Comparison of Speeds
- Smart DNS: Offers the fastest speeds due to no encryption.
- Proxy Servers: Typically faster than VPNs but slower compared to Smart DNS.
- Tor: Generally the slowest due to its multi-layer encryption process.
Security and Privacy Overview
- Tor and SSH provide superior anonymity.
- Smart DNS comes with minimal privacy protection.
- Proxy Servers vary widely in terms of security, based on the selected type and provider.
Financial Aspects
- Smart DNS and Proxy Servers often include free options.
- Remote Desktop solutions might be costly for frequent usage.
User Friendliness
- Smart DNS: Very easy to set up.
- Tor: Simple to install, but may be slower.
- SSH and Remote Desktop require more advanced knowledge and skills.
Final Thoughts
While VPNs have long been a favored method for internet security, they aren’t the only option available. If you’re prioritizing speed, adaptability, or affordability, consider exploring solutions such as Smart DNS, proxy servers, Tor, remote desktops, and SSH tunneling, each offering distinct advantages. Select the approach that best meets your preferences and enjoy a more secure and private online experience.
Images Credit: Pcmobitech.com