Understanding Various Phishing Attack Types and Their Targeting Methods
As phishing attacks continue to rise globally, they have become one of the most challenging threats in the online environment. In its latest report, the FBI highlighted that Americans lost more than $12.5 billion to phishing scams in 2023 alone. While email phishing remains the most prevalent method, attackers are employing increasingly diverse strategies to steal sensitive information. This article explores the various types of phishing attacks, their tactics, and effective measures to safeguard against them.
Understanding Phishing
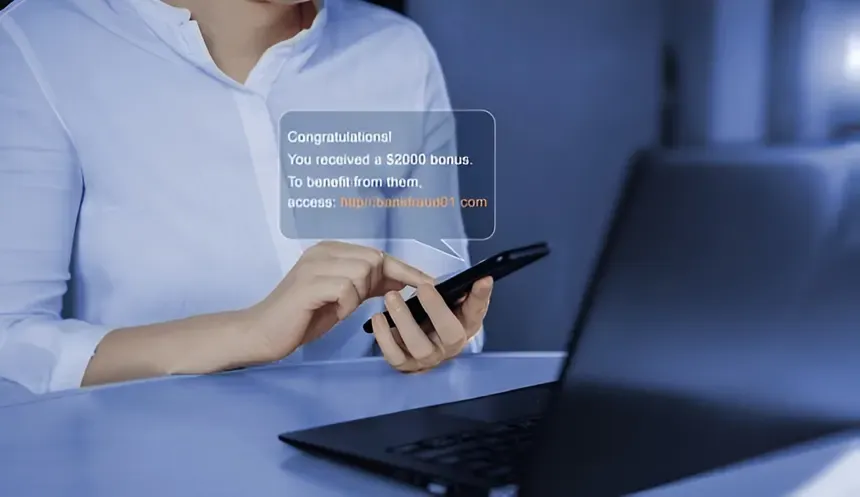
Image Credit: ShutterStock
Phishing encompasses various deceptive tactics employed by cybercriminals to trick individuals into revealing personal, financial, or login credentials. Attackers frequently impersonate reputable organizations or trusted contacts, crafting messages that appear legitimate and compelling. This deception encourages victims to click malicious links, download infected files, or share sensitive information unwittingly.
The Escalation of Phishing Attacks
The boom in digital interaction has significantly heightened the incidence of phishing schemes. Today’s phishing communications are almost indistinguishable from authentic messages, thanks in part to advancements in generative AI and other sophisticated technologies. In contrast to earlier phishing attempts, which were often poorly executed, modern tactics involve highly persuasive content that can deceive even those well-versed in technology.
Categories of Phishing Attacks
Phishing manifests in several distinct forms, each utilizing specific strategies to ensnare targets. Below are some of the most common types:
1. Email Phishing
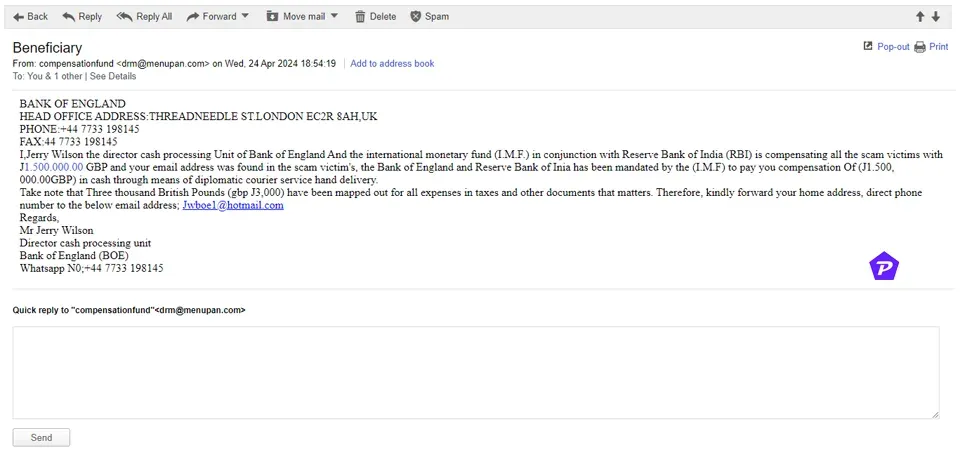
Email phishing represents one of the oldest yet most widely used tactics, targeting individuals through seemingly credible emails. Cybercriminals typically fabricate emails appearing to originate from trusted institutions such as banks, government bodies, or well-known retailers.
Identifying Characteristics:
- Requests for users to click links, download attachments, or divulge login details.
- Crafted to be highly convincing due to AI technology, making detection difficult.
- Utilizes official logos, realistic subject lines, and personalized greetings.
Protection Measures:
- Always verify the sender’s email address.
- Refrain from clicking on links or attachments from unknown sources.
- Contact organizations directly if there is suspicion of fraudulent activity.
2. Smishing
Smishing, or SMS phishing, employs text messages to execute phishing attacks. Given the common perception that texts are personal or urgent, smishing scams tend to yield high success rates.
Common Smishing Tactics:
- Messages about package deliveries, often containing tracking links.
- Alerts from “banks” indicating unusual account activity.
- Messages from unknown numbers trying to initiate a conversation.
Example: Pig Butchering
A well-known smishing scam where perpetrators build rapport over time, ultimately convincing the victim to invest in a bogus cryptocurrency platform.
Protection Tips:
- Avoid clicking on links in unsolicited messages.
- Confirm alerts by visiting the official websites or apps directly.
- Utilize anti-spam filters available on most mobile devices.
3. Angler Phishing
Angler phishing occurs primarily on social media platforms, where attackers pose as legitimate customer service representatives to exploit users seeking assistance or reporting issues.
How It Works:
- Scammer impersonates a customer service account, offering a “solution” to your problem.
- May provide a link to a spoofed login page to harvest your credentials.
Recognizing Angler Phishing:
- Watch for slight variations in usernames (extra letters or symbols).
- Verify social media accounts before divulging personal information.
- Respond only to verified accounts that display a blue checkmark.
4. Vishing
Vishing, or voice phishing, involves attackers calling individuals while pretending to be from reputable organizations such as banks or government agencies.
Methodology of Vishing:
- Attackers create urgency, claiming scenarios like fraud alerts or technical difficulties.
- They may request personal details such as Social Security numbers or account information.
Defensive Measures Against Vishing:
- End the call and directly contact the organization’s official support number.
- Be suspicious of unsolicited calls that request personal information.
- Make use of scam-blocking features available on most smartphones.
5. Spear Phishing
Spear phishing differs from traditional phishing by targeting specific individuals or groups. Attackers gather detailed information on victims, such as their job roles or recent affiliations, to craft convincing communications.
Specialized Targeting:
- Whaling: A variant of spear phishing aimed at high-profile individuals such as executives.
Scenario Example:
- Receiving a request from a known colleague for sensitive information or to expedite a financial transaction.
Protection Strategies:
- Confirm requests from colleagues through alternative communication methods.
- Exercise caution regarding unusual requests, even if they appear to come from trusted contacts.
6. Watering Hole Attacks
In a watering hole attack, attackers compromise a frequently visited trusted website, embedding malware or malicious links within the site’s code.
Effectiveness of Watering Hole Attacks:
- Victims unknowingly visit compromised sites.
- Attackers tend to target websites that align with particular demographics.
Prevention Advice:
- Keep your browser and security software updated regularly.
- Limit interactions with websites exhibiting unusual behaviors, such as excessive pop-ups or redirects.
7. Website Spoofing
Website spoofing involves creating a fraudulent website that mimics a legitimate one, tricking users into inputting their sensitive information. Typosquatting, where attackers utilize domain names similar to those of popular sites, is a frequent tactic used in these attacks.
Mechanism of Spoofed Websites:
- Users may inadvertently visit a fake site due to mistyped URLs (e.g., “Amazonn.com” vs. “Amazon.com” ).
- Spoofed sites, while appearing legitimate, are specifically designed to capture login credentials and other sensitive data.
Defensive Measures:
- Double-check URLs prior to entering any personal information.
- Enable two-factor authentication for sensitive accounts.
- Utilize a password manager to confirm the legitimacy of visited sites.
Signs of Phishing Attacks
Identifying potential phishing attempts can significantly reduce the risk of becoming a victim. Here are common warning signs:
- Unusual Email Addresses: Watch for misspellings or extraneous characters in the domain name.
- Urgent Requests: Phishing messages typically urge immediate actions.
- Generic Greetings: Beware of messages that use generic phrases like “Dear Customer” .
- Unexpected Attachments or Links: Do not click on attachments from unknown sources.
- Language Errors: Phishing attempts may still exhibit grammatical or spelling mistakes.
Effective Countermeasures Against Phishing Attacks
- Enable Multi-Factor Authentication (MFA):
- Implementing MFA provides an additional security layer, complicating unauthorized access to accounts.
- Inform Yourself and Others:
- Stay updated on phishing tactics and educate family and colleagues on identifying suspicious communications.
- Leverage Anti-Phishing Solutions:
- Many email providers have built-in phishing detection systems. Additionally, antivirus software offers anti-phishing features.
- Verify Information Requests:
- Any request for sensitive information should be verified through an official channel.
- Keep Software Up-to-Date:
- Regular updates ensure protection against known vulnerabilities.
Concluding Thoughts
The landscape of phishing has expanded from basic email scams to a complex array of online threats targeting users across different platforms. A thorough understanding of each phishing variant—from smishing to watering hole attacks—equips individuals with the knowledge to identify and evade these dangers. By maintaining vigilance and adopting preventative measures, one can significantly minimize the risk of falling victim to these increasingly sophisticated cyber threats.